From Dark Reading:
Businesses Not Properly Securing Microsoft Active Directory
"Businesses overlook key security aspects of AD, leaving sensitive data open to external and internal attacks, new study shows.
Microsoft Active Directory (AD) often lulls enterprises into a false sense of security. Many are so confident in the system's security measures they neglect to put the right safeguards in place."
The purpose of this blog is to help small-medium businesses (SMB's) deal effectively with their unique cyber security needs. With over 15 years experience in IT and cyber security I will show SMB's how they can leverage their limited resources to develop effective cyber defenses to the most common threats using information security best practices and no/low cost tools.
LinkedIn: http://www.linkedin.com/in/ecissorsky/
Twitter: @ecissorsky
Thursday, May 11, 2017
10 Free or Low-Cost Security Tools
From Dark Reading:
10 Free or Low-Cost Security Tools
"Security spending is on the rise, but allocating funds remains a challenge. Systems are expensive and skilled talent — if you can find it — comes at a high price.
A new wave of tools, from low-cost to free open source software (FOSS), aim to help with tasks like network scanning and penetration testing. Some of these tools are tailored for specific purposes while others cross several domains."
10 Free or Low-Cost Security Tools
"Security spending is on the rise, but allocating funds remains a challenge. Systems are expensive and skilled talent — if you can find it — comes at a high price.
A new wave of tools, from low-cost to free open source software (FOSS), aim to help with tasks like network scanning and penetration testing. Some of these tools are tailored for specific purposes while others cross several domains."
US-CERT Alert: FTC Announces Resource for Small Business Owners
From US-CERT:
FTC Announces Resource for Small Business Owners
"The Federal Trade Commission (FTC) has released an announcement about its new website devoted to protecting small businesses. This resource aims to help business owners avoid scams, protect their computers and networks, and keep their customers' and employees' data safe."
FTC Announces Resource for Small Business Owners
"The Federal Trade Commission (FTC) has released an announcement about its new website devoted to protecting small businesses. This resource aims to help business owners avoid scams, protect their computers and networks, and keep their customers' and employees' data safe."
US-CERT Alert: Microsoft Releases May 2017 Security Updates
From US-CERT:
Microsoft Releases May 2017 Security Updates
"Microsoft has released updates to address vulnerabilities in Microsoft software. A remote attacker could exploit some of these vulnerabilities to take control of a system."
Microsoft Releases May 2017 Security Updates
"Microsoft has released updates to address vulnerabilities in Microsoft software. A remote attacker could exploit some of these vulnerabilities to take control of a system."
US-CERT Alert: Cisco Releases Security Update
From US-CERT:
Cisco Releases Security Update
"Cisco has released a security update to address a vulnerability in its WebEx Meetings Server which could allow a remote attacker to obtain sensitive information."
Cisco Releases Security Update
"Cisco has released a security update to address a vulnerability in its WebEx Meetings Server which could allow a remote attacker to obtain sensitive information."
Lawyers demand answers after artist forced to unlock his phone
From Sophos Naked Security:
Lawyers demand answers after artist forced to unlock his phone
"In February, artist Aaron Gach flew home to San Francisco after putting on a gallery installation in Brussels.
The show, titled Center for Tactical Magic, focused on “mass incarceration, government control, and political dissent”."
Lawyers demand answers after artist forced to unlock his phone
"In February, artist Aaron Gach flew home to San Francisco after putting on a gallery installation in Brussels.
The show, titled Center for Tactical Magic, focused on “mass incarceration, government control, and political dissent”."
The Google Play apps that say they don’t collect your data – and then do
From Sophos Naked Security:
The Google Play apps that say they don’t collect your data – and then do
"Adware is typically viewed as a nuisance that does no real harm. But in recent research, SophosLabs has seen adware in Google Play that does more than just deliver ads. This strain can collect the user’s personal information, including email address, and send them to a remote server.
Sophos detects this adware library as Android XavirAd and the information-stealing component as Andr/Infostl-BK."
The Google Play apps that say they don’t collect your data – and then do
"Adware is typically viewed as a nuisance that does no real harm. But in recent research, SophosLabs has seen adware in Google Play that does more than just deliver ads. This strain can collect the user’s personal information, including email address, and send them to a remote server.
Sophos detects this adware library as Android XavirAd and the information-stealing component as Andr/Infostl-BK."
How to hack a Jeep Cherokee – but don’t try this at home, kids
From Sophos Naked Security:
How to hack a Jeep Cherokee – but don’t try this at home, kids
"Charlie Miller and Chris Valasek originally hacked a Jeep Cherokee in 2015, physically controlling it – and a nervous journalist occupying it – on the highway. FCA, the company that makes the Cherokee, recalled 1.4m of them and issued a patch. In response, the pair hacked that one, too, and gained more control, rather than less. Earlier this year, they put all their notes online, which most of us missed until Valasek tweeted it."
How to hack a Jeep Cherokee – but don’t try this at home, kids
"Charlie Miller and Chris Valasek originally hacked a Jeep Cherokee in 2015, physically controlling it – and a nervous journalist occupying it – on the highway. FCA, the company that makes the Cherokee, recalled 1.4m of them and issued a patch. In response, the pair hacked that one, too, and gained more control, rather than less. Earlier this year, they put all their notes online, which most of us missed until Valasek tweeted it."
Unhappy 39th birthday, spam, and many unhappy returns
From Sophos Naked Security:
Unhappy 39th birthday, spam, and many unhappy returns
"In October 2011, email turned 40. Last week it was the turn of its troublesome twin, spam, to make it to within a year of the same hoary milestone.
Inevitably in an industry ageing fast, personal computing’s calendar is filling up with significant anniversaries. So, does spam’s – or email’s – really matter that much?"
Unhappy 39th birthday, spam, and many unhappy returns
"In October 2011, email turned 40. Last week it was the turn of its troublesome twin, spam, to make it to within a year of the same hoary milestone.
Inevitably in an industry ageing fast, personal computing’s calendar is filling up with significant anniversaries. So, does spam’s – or email’s – really matter that much?"
One more way to get busted on the Dark Web
From Sophos Naked Security:
One more way to get busted on the Dark Web
"Tor users suspected of child abuse imagery may have visited an outside file-sharing service simply because Tor’s so slow at routing traffic.
As Motherboard reports, the US Department of Homeland Security (DHS) identified several Tor users suspected of using a dark web site to post links to child abuse imagery that was hosted on a file-sharing service."
One more way to get busted on the Dark Web
"Tor users suspected of child abuse imagery may have visited an outside file-sharing service simply because Tor’s so slow at routing traffic.
As Motherboard reports, the US Department of Homeland Security (DHS) identified several Tor users suspected of using a dark web site to post links to child abuse imagery that was hosted on a file-sharing service."
Tuesday, May 9, 2017
3 Reasons Why TheDarkOverlord Loves Vendor Data Breaches
From PivotPoint Security:
3 Reasons Why TheDarkOverlord Loves Vendor Data Breaches
As you may well have heard by now, TDO made headlines recently when they posted most of the new, unreleased episodes of the hit Netflix original “Orange is the New Black” online when Netflix refused to pay a ransom."
3 Reasons Why TheDarkOverlord Loves Vendor Data Breaches
As you may well have heard by now, TDO made headlines recently when they posted most of the new, unreleased episodes of the hit Netflix original “Orange is the New Black” online when Netflix refused to pay a ransom."
MSFTSecurity Virtual Security Summit
Date: Wednesday, May 10th Time: 8:00am-10:15am PT / 11:00am-1:15pm ET
On May 10th, join leading experts as we live stream from the CISO Summit, an invitation-only event for Chief Information Security Officers of large enterprises. For the first time, we’re making this exclusive content available for you to view online.
It’s no surprise that cybersecurity will continue to be a top issue for executives, IT and security professionals in 2017. The threats are wide-ranging and plentiful, but there are best practices and solutions you can adopt to keep your organization safe.
Silverpush Quits Creeping World Out, Ceases Tracking TV Habits Via Inaudible 'Beacons'
A follow up to two (2) previous posts. From Forbes:
Silverpush Quits Creeping World Out, Ceases Tracking TV Habits Via Inaudible 'Beacons'
"Less than a week after the Federal Trade Commission warned app developers to stop using code that listened for inaudible sound to track mobile owners' TV watching habits, the Indian firm that marketed the product tells FORBES it's killing the software. But Silverpush product manager Piyush Bhatt says it's not ending the Unique Audio Beacon service because of that FTC action, or because of the many privacy concerns raised over the last year. It's simply a "business decision"."
Silverpush Quits Creeping World Out, Ceases Tracking TV Habits Via Inaudible 'Beacons'
"Less than a week after the Federal Trade Commission warned app developers to stop using code that listened for inaudible sound to track mobile owners' TV watching habits, the Indian firm that marketed the product tells FORBES it's killing the software. But Silverpush product manager Piyush Bhatt says it's not ending the Unique Audio Beacon service because of that FTC action, or because of the many privacy concerns raised over the last year. It's simply a "business decision"."
Are you encrypting your documents? Here’s what happens when you don’t
From Sophos Naked Security:
Are you encrypting your documents? Here’s what happens when you don’t
"In June 2015, someone connected to Plymouth University accidentally sent a spreadsheet containing the salaries, pensions and allowances of 245 senior staff to the wrong email address.
The error was reported to the UK’s Information Commissioner (ICO), and the file was said to have been deleted by the recipient. Until, that is, the same file turned up last week in the inbox of a local newspaper from an anonymous source."
Are you encrypting your documents? Here’s what happens when you don’t
"In June 2015, someone connected to Plymouth University accidentally sent a spreadsheet containing the salaries, pensions and allowances of 245 senior staff to the wrong email address.
The error was reported to the UK’s Information Commissioner (ICO), and the file was said to have been deleted by the recipient. Until, that is, the same file turned up last week in the inbox of a local newspaper from an anonymous source."
Dating site users spammed with smut after ‘third-party’ data leak
From Sophos Naked Security:
Dating site users spammed with smut after ‘third-party’ data leak
"Users of the Guardian’s Soulmates dating site have been getting spammed with smut after the site leaked their contact information.
The UK-based Guardian newspaper’s publisher, which runs the service, is blaming “human error” and a third-party technology provider for the leak, which has now been fixed. According to the BBC, the site — which charges users up to £32 ($41.50) per month — said that only email addresses and user IDs had been exposed directly. But that information can be used to dig out more from public profiles, said the company, including photos, relationship preferences and physical descriptions."
Dating site users spammed with smut after ‘third-party’ data leak
"Users of the Guardian’s Soulmates dating site have been getting spammed with smut after the site leaked their contact information.
The UK-based Guardian newspaper’s publisher, which runs the service, is blaming “human error” and a third-party technology provider for the leak, which has now been fixed. According to the BBC, the site — which charges users up to £32 ($41.50) per month — said that only email addresses and user IDs had been exposed directly. But that information can be used to dig out more from public profiles, said the company, including photos, relationship preferences and physical descriptions."
Android Apps Secretly Tracking Users By Listening To Inaudible Sound Hidden In Adverts
From The Independent:
Android Apps Secretly Tracking Users By Listening To Inaudible Sound Hidden In Adverts
"Researchers say the technique can even be used to de-anonymise Tor users
An increasing number of Android applications are attempting to track users without their knowledge, according to a new report.
Over recent years, companies have started hiding “beacons”, ultrasonic audio signals inaudible to humans, in their adverts, in order to track devices and learn more about their owners."
Android Apps Secretly Tracking Users By Listening To Inaudible Sound Hidden In Adverts
"Researchers say the technique can even be used to de-anonymise Tor users
An increasing number of Android applications are attempting to track users without their knowledge, according to a new report.
Over recent years, companies have started hiding “beacons”, ultrasonic audio signals inaudible to humans, in their adverts, in order to track devices and learn more about their owners."
SPY PHONE Secret messages hidden in TV adverts can order smartphones to spy on people, researchers warn
From The Sun:
SPY PHONE Secret messages hidden in TV adverts can order smartphones to spy on people, researchers warn
"Popular apps downloaded by millions of people are always on the look out for clandestine broadcasts which order them to begin snooping on citizens."
SPY PHONE Secret messages hidden in TV adverts can order smartphones to spy on people, researchers warn
"Popular apps downloaded by millions of people are always on the look out for clandestine broadcasts which order them to begin snooping on citizens."
This ‘dark web’ vigilante is zapping tons of child porn
From the NY Post:
This ‘dark web’ vigilante is zapping tons of child porn
"The dark web is now 20 percent lighter — thanks to a “Mr. Robot”-like vigilante hacker who has zapped one-fifth of its content in a crusade against child porn.
“Action had to be taken,” the unnamed hacker told the blog Motherboard.com, adding that he or she is a complete novice."
This ‘dark web’ vigilante is zapping tons of child porn
"The dark web is now 20 percent lighter — thanks to a “Mr. Robot”-like vigilante hacker who has zapped one-fifth of its content in a crusade against child porn.
“Action had to be taken,” the unnamed hacker told the blog Motherboard.com, adding that he or she is a complete novice."
US-CERT Alert: Security Tip (ST05-019) Preventing and Responding to Identity Theft
Privacy Week follow up from US-CERT:
Security Tip (ST05-019) Preventing and Responding to Identity Theft
Is identity theft just a problem for people who submit information online?
You can be a victim of identity theft even if you never use a computer. Malicious people may be able to obtain personal information (such as credit card numbers, phone numbers, account numbers, and addresses) by stealing your wallet, overhearing a phone conversation, rummaging through your trash (a practice known as dumpster diving), or picking up a receipt at a restaurant that has your account number on it. If a thief has enough information, he or she may be able to impersonate you to purchase items, open new accounts, or apply for loans.
Security Tip (ST05-019) Preventing and Responding to Identity Theft
Is identity theft just a problem for people who submit information online?
You can be a victim of identity theft even if you never use a computer. Malicious people may be able to obtain personal information (such as credit card numbers, phone numbers, account numbers, and addresses) by stealing your wallet, overhearing a phone conversation, rummaging through your trash (a practice known as dumpster diving), or picking up a receipt at a restaurant that has your account number on it. If a thief has enough information, he or she may be able to impersonate you to purchase items, open new accounts, or apply for loans.
US-CERT Alert: Security Tip (ST04-014) Avoiding Social Engineering and Phishing Attacks
Privacy Week follow up from US-CERT:
Security Tip (ST04-014) Avoiding Social Engineering and Phishing Attacks
What is a social engineering attack?
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offering credentials to support that identity. However, by asking questions, he or she may be able to piece together enough information to infiltrate an organization's network. If an attacker is not able to gather enough information from one source, he or she may contact another source within the same organization and rely on the information from the first source to add to his or her credibility.
Security Tip (ST04-014) Avoiding Social Engineering and Phishing Attacks
What is a social engineering attack?
In a social engineering attack, an attacker uses human interaction (social skills) to obtain or compromise information about an organization or its computer systems. An attacker may seem unassuming and respectable, possibly claiming to be a new employee, repair person, or researcher and even offering credentials to support that identity. However, by asking questions, he or she may be able to piece together enough information to infiltrate an organization's network. If an attacker is not able to gather enough information from one source, he or she may contact another source within the same organization and rely on the information from the first source to add to his or her credibility.
US-CERT Alert: Security Tip (ST04-013) Protecting Your Privacy
Privacy Week follow up from US-CERT:
Security Tip (ST04-013) Protecting Your Privacy
How do you know if your privacy is being protected?
Security Tip (ST04-013) Protecting Your Privacy
How do you know if your privacy is being protected?
- Privacy policy – Before submitting your name, email address, or other personal information on a website, look for the site's privacy policy. This policy should state how the information will be used and whether or not the information will be distributed to other organizations. Companies sometimes share information with partner vendors who offer related products or may offer options to subscribe to particular mailing lists. Look for indications that you are being added to mailing lists by default—failing to deselect those options may lead to unwanted spam. If you cannot find a privacy policy on a website, consider contacting the company to inquire about the policy before you submit personal information, or find an alternate site. Privacy policies sometimes change, so you may want to review them periodically.
US-CERT Alert: Security Tip (ST06-008) Safeguarding Your Data
Privacy Week follow up from US-CERT:
Security Tip (ST06-008) Safeguarding Your Data
"Why isn't "more" better?
Maybe there is an extra software program included with a program you bought. Or perhaps you found a free download online. You may be tempted to install the programs just because you can, or because you think you might use them later. However, even if the source and the software are legitimate, there may be hidden risks. And if other people use your computer, there are additional risks."
Security Tip (ST06-008) Safeguarding Your Data
"Why isn't "more" better?
Maybe there is an extra software program included with a program you bought. Or perhaps you found a free download online. You may be tempted to install the programs just because you can, or because you think you might use them later. However, even if the source and the software are legitimate, there may be hidden risks. And if other people use your computer, there are additional risks."
US-CERT Alert: FTC Promotes Privacy Awareness Week
From US-CERT:
FTC Promotes Privacy Awareness Week
FTC Promotes Privacy Awareness Week
US-CERT Alert: Microsoft Releases Critical Security Update
From US-CERT:
Microsoft Releases Critical Security Update
Users and administrators are encouraged to review Microsoft Security Advisory 4022344(link is external) for details and apply the necessary update."
Microsoft Releases Critical Security Update
Users and administrators are encouraged to review Microsoft Security Advisory 4022344(link is external) for details and apply the necessary update."
Monday, May 8, 2017
Homeland Security Issues Warning on Cyberattack Campaign
From DataBreach Today:
Homeland Security Issues Warning on Cyberattack Campaign
"The Department of Homeland Security is warning IT services providers, healthcare organizations and three other business sectors about a sophisticated cyberattack campaign that involves using stolen administrative credentials and implanting malware, including PLUGX/SOGU and RedLeaves, on critical systems."
Homeland Security Issues Warning on Cyberattack Campaign
"The Department of Homeland Security is warning IT services providers, healthcare organizations and three other business sectors about a sophisticated cyberattack campaign that involves using stolen administrative credentials and implanting malware, including PLUGX/SOGU and RedLeaves, on critical systems."
Monsanto accused of hiring army of trolls to silence online dissent – court papers
From RT:
Monsanto accused of hiring army of trolls to silence online dissent – court papers
"Biotech giant Monsanto is being accused of hiring, through third parties, an army of Internet trolls to counter negative comments, while citing positive “ghost-written” pseudo-scientific reports which downplay the potential risks of their products.
The documents emerged during pre-trials on 50 lawsuits against Monsanto which were pending in the US District Court in San Francisco. The plaintiffs allege that exposure to the biotech giant’s flagship product, the herbicide Roundup, caused them or their relatives to develop non-Hodgkin lymphoma, while Monsanto concealed the potential risks."
Monsanto accused of hiring army of trolls to silence online dissent – court papers
"Biotech giant Monsanto is being accused of hiring, through third parties, an army of Internet trolls to counter negative comments, while citing positive “ghost-written” pseudo-scientific reports which downplay the potential risks of their products.
The documents emerged during pre-trials on 50 lawsuits against Monsanto which were pending in the US District Court in San Francisco. The plaintiffs allege that exposure to the biotech giant’s flagship product, the herbicide Roundup, caused them or their relatives to develop non-Hodgkin lymphoma, while Monsanto concealed the potential risks."
The U.S. military is targeting Islamic State's virtual caliphate by hunting & killing its online operatives one-by-one
From the LA Times:
The U.S. military is targeting Islamic State's virtual caliphate by hunting & killing its online operatives one-by-one
"The months-long manhunt for French-born Rachid Kassim ended one chilly morning early this year when a drone-launched missile destroyed his battered white pickup truck as it motored through the besieged Iraqi city of Mosul.
The 29-year-old former rapper had cast a grim shadow in international counter-terrorism circles. He spoke fluent French, once beheaded a man in an online video and played a role in a string of terrorist plots — two successful — in France last year."
The U.S. military is targeting Islamic State's virtual caliphate by hunting & killing its online operatives one-by-one
"The months-long manhunt for French-born Rachid Kassim ended one chilly morning early this year when a drone-launched missile destroyed his battered white pickup truck as it motored through the besieged Iraqi city of Mosul.
The 29-year-old former rapper had cast a grim shadow in international counter-terrorism circles. He spoke fluent French, once beheaded a man in an online video and played a role in a string of terrorist plots — two successful — in France last year."
What Can You Learn On Your Own
From SANS ISC:
What Can You Learn On Your Own
"We are all privileged to work in the field of information security. We also carry the responsibility to keep current in our chosen profession. Regularly I hear from fellow colleagues who want to learn something, but do not have a training budget, feel powerless and sometimes give up. I would like to share several approaches that can be used to bridge this gap and will hopefully inspire a self-investment both this weekend and beyond. None of these ideas cost anything more than time.
I decided to borrow an idea from an informal mentor, something I generally give them credit for, but not always. I decided to wake up early each morning with the intent to learn something new every day. Maybe the something is a new tool, a new linux distribution or taking an online class. Having done this now for the last 7 years, I can say without hesitation or regret that it has been pivotal in making me a better me. I am convinced that applying just a little bit of incremental effort will serve you well as well."
What Can You Learn On Your Own
"We are all privileged to work in the field of information security. We also carry the responsibility to keep current in our chosen profession. Regularly I hear from fellow colleagues who want to learn something, but do not have a training budget, feel powerless and sometimes give up. I would like to share several approaches that can be used to bridge this gap and will hopefully inspire a self-investment both this weekend and beyond. None of these ideas cost anything more than time.
I decided to borrow an idea from an informal mentor, something I generally give them credit for, but not always. I decided to wake up early each morning with the intent to learn something new every day. Maybe the something is a new tool, a new linux distribution or taking an online class. Having done this now for the last 7 years, I can say without hesitation or regret that it has been pivotal in making me a better me. I am convinced that applying just a little bit of incremental effort will serve you well as well."
‘Playpen’ Creator Sentenced to 30 Years
Even on the Dark Web with Tor - You. Will. Get. Caught.
From the FBI:
‘Playpen’ Creator Sentenced to 30 Years
Steven W. Chase, 58, of Naples, Florida, created a website called Playpen in August 2014 on the Tor network, an open network on the Internet where users can communicate anonymously through “hidden service” websites—where criminal activity is not uncommon. Chase ran the Playpen website, where members uploaded and viewed tens of thousands of postings of young victims, indexed by age, sex, and the type of sexual activity involved."
From the FBI:
‘Playpen’ Creator Sentenced to 30 Years
Steven W. Chase, 58, of Naples, Florida, created a website called Playpen in August 2014 on the Tor network, an open network on the Internet where users can communicate anonymously through “hidden service” websites—where criminal activity is not uncommon. Chase ran the Playpen website, where members uploaded and viewed tens of thousands of postings of young victims, indexed by age, sex, and the type of sexual activity involved."
WikiLeaks Details MitM Attack Tool Used by CIA
From Security Week:
WikiLeaks Details MitM Attack Tool Used by CIA
The tool, initially called Fulcrum and later renamed Archimedes by its developers, can be used to conduct MitM attacks within a local area network (LAN). The leaked documents, dated between 2011 and 2014, describe it as a tool that allows the user to redirect LAN traffic from a targeted computer through an attacker-controlled machine before it’s passed on to the gateway."
WikiLeaks Details MitM Attack Tool Used by CIA
The tool, initially called Fulcrum and later renamed Archimedes by its developers, can be used to conduct MitM attacks within a local area network (LAN). The leaked documents, dated between 2011 and 2014, describe it as a tool that allows the user to redirect LAN traffic from a targeted computer through an attacker-controlled machine before it’s passed on to the gateway."
Google Researchers Find "Worst" Windows RCE Flaw
From Security Week:
Google Researchers Find "Worst" Windows RCE Flaw
"Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich claim to have found a critical vulnerability in Windows. The details of the flaw will likely be disclosed in 90 days from now even if a patch is not available.
Ormandy announced over the weekend on Twitter that he and Silvanovich had discovered “the worst Windows remote code exec [vulnerability] in recent memory.”
Google Researchers Find "Worst" Windows RCE Flaw
"Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich claim to have found a critical vulnerability in Windows. The details of the flaw will likely be disclosed in 90 days from now even if a patch is not available.
Ormandy announced over the weekend on Twitter that he and Silvanovich had discovered “the worst Windows remote code exec [vulnerability] in recent memory.”
Exploitable Details of Intel's 'Apocalyptic' AMT Firmware Vulnerability Disclosed
The Intel AMT firmware vulnerability is much more serious than previously reported. From Security Week:
Exploitable Details of Intel's 'Apocalyptic' AMT Firmware Vulnerability Disclosed
Details of the Intel AMT firmware vulnerability announced on May 1, 2017 are now public knowledge; and the suggestion that 'this is somewhere between nightmarish and apocalyptic' has been proven correct.
One day after Intel's alert, Embedi (the firm that discovered the vulnerability back in February this year) published a brief note. One particular sentence stood out to researchers at Tenable: "With 100 percent certainty it is not an RCE but rather a logical vulnerability."
Exploitable Details of Intel's 'Apocalyptic' AMT Firmware Vulnerability Disclosed
Details of the Intel AMT firmware vulnerability announced on May 1, 2017 are now public knowledge; and the suggestion that 'this is somewhere between nightmarish and apocalyptic' has been proven correct.
One day after Intel's alert, Embedi (the firm that discovered the vulnerability back in February this year) published a brief note. One particular sentence stood out to researchers at Tenable: "With 100 percent certainty it is not an RCE but rather a logical vulnerability."
Software Download Mirror Distributes Mac Malware
From Security Week:
Software Download Mirror Distributes Mac Malware
The company has posted a security alert on its website, informing Mac users that from Tuesday to Saturday of last week they might have downloaded a Trojanized version of the application. According to HandBrake, while not all users might have been affected, all of them should verify the downloaded file before running it."
Software Download Mirror Distributes Mac Malware
The company has posted a security alert on its website, informing Mac users that from Tuesday to Saturday of last week they might have downloaded a Trojanized version of the application. According to HandBrake, while not all users might have been affected, all of them should verify the downloaded file before running it."
Defining Your Overarching Goal for Email Phishing Testing
Great article by Kevin Beaver on Toolbox.com:
Defining Your Overarching Goal for Email Phishing Testing
Defining Your Overarching Goal for Email Phishing Testing
US-CERT Alert: Mozilla Releases Security Updates
From US-CERT:
Mozilla Releases Security Updates
Mozilla Releases Security Updates
US-CERT Alert: Intel Firmware Vulnerability
More on the Intel AMT vulnerability from US-CERT:
Intel Firmware Vulnerability
"Intel has released recommendations to address a vulnerability in the firmware of the following Intel products: Active Management Technology, Standard Manageability, and Small Business Technology firmware versions 6.x, 7.x, 8.x, 9.x, 10.x, 11.0, 11.5, and 11.6. This vulnerability does not affect Intel-based consumer PCs. An attacker could exploit this vulnerability to take control of an affected system."
Intel Firmware Vulnerability
"Intel has released recommendations to address a vulnerability in the firmware of the following Intel products: Active Management Technology, Standard Manageability, and Small Business Technology firmware versions 6.x, 7.x, 8.x, 9.x, 10.x, 11.0, 11.5, and 11.6. This vulnerability does not affect Intel-based consumer PCs. An attacker could exploit this vulnerability to take control of an affected system."
And Now a Ransomware Tool That Charges Based On Where You Live
From Dark Reading:
And Now a Ransomware Tool That Charges Based On Where You Live
"Malware is designed to charge more for victims in countries with a higher cost of living, Recorded Future says.
The creators of "Fatboy," a new and somewhat politically incorrectly named ransomware tool that surfaced recently on a Russian crimeware forum, appear to have adopted an interesting economic approach in designing the malware."
And Now a Ransomware Tool That Charges Based On Where You Live
"Malware is designed to charge more for victims in countries with a higher cost of living, Recorded Future says.
The creators of "Fatboy," a new and somewhat politically incorrectly named ransomware tool that surfaced recently on a Russian crimeware forum, appear to have adopted an interesting economic approach in designing the malware."
How to protect your boss from phishing attacks
From Sophos Naked Security:
How to protect your boss from phishing attacks
"We already know that more than 75% of us lie on social media.
Too bad it’s impracticable to lie more about our workplaces on professional networking sites like LinkedIn: it might spare our employers a lot of grief."
How to protect your boss from phishing attacks
"We already know that more than 75% of us lie on social media.
Too bad it’s impracticable to lie more about our workplaces on professional networking sites like LinkedIn: it might spare our employers a lot of grief."
French Cybersecurity Agency to Probe Macron Hacking Attack
From Newsmax:
French Cybersecurity Agency to Probe Macron Hacking Attack
"France's election campaign commission said Saturday "a significant amount of data" — and some fake information — has been leaked on social networks following a hacking attack on centrist Emmanuel Macron's presidential campaign. It urged citizens not to relay the data on social media to protect the integrity of the French vote."
French Cybersecurity Agency to Probe Macron Hacking Attack
"France's election campaign commission said Saturday "a significant amount of data" — and some fake information — has been leaked on social networks following a hacking attack on centrist Emmanuel Macron's presidential campaign. It urged citizens not to relay the data on social media to protect the integrity of the French vote."
Law Firm Sues Insurer Over Income Loss in Ransomware Attack
From Dark Reading:
Law Firm Sues Insurer Over Income Loss in Ransomware Attack
"A Rhode Island law firm sued its insurer over failing to pay for lost income following a ransomware attack on the firm.
A small Rhode Island law firm filed a lawsuit against its insurance company after the insurer refused to pay $700,000 in lost billings following a ransomware attack on the firm, according to a report in the Providence Journal."
Law Firm Sues Insurer Over Income Loss in Ransomware Attack
"A Rhode Island law firm sued its insurer over failing to pay for lost income following a ransomware attack on the firm.
A small Rhode Island law firm filed a lawsuit against its insurance company after the insurer refused to pay $700,000 in lost billings following a ransomware attack on the firm, according to a report in the Providence Journal."
How does Ticketbleed affect session ID security?
Looks like this one is going to get a lot of media coverage. From Search Security:
How does Ticketbleed affect session ID security?
"The Ticketbleed bug in some F5 Networks products caused session IDs and uninitialized memory to leak. Expert Judith Myerson explains what a session ID is and how attackers use it.
How does Ticketbleed affect session ID security?
"The Ticketbleed bug in some F5 Networks products caused session IDs and uninitialized memory to leak. Expert Judith Myerson explains what a session ID is and how attackers use it.
Friday, May 5, 2017
FBI's James Comey on Insider Threat, Other Cyber Challenges
From DataBreach Today:
FBI's James Comey on Insider Threat, Other Cyber Challenges
The latest ISMG Security Report leads with an account of FBI Director James Comey's testimony before the U.S. Congress on insiders posing a cyberthreat to the American law enforcement bureau.
In the Security Report, you'll also hear (click on player beneath image to listen):
FBI's James Comey on Insider Threat, Other Cyber Challenges
The latest ISMG Security Report leads with an account of FBI Director James Comey's testimony before the U.S. Congress on insiders posing a cyberthreat to the American law enforcement bureau.
In the Security Report, you'll also hear (click on player beneath image to listen):
- ISMG Security and Technology Editor Jeremy Kirk report on initiatives in Australia to get businesses to share cyberthreat intelligence, and;
- An explanation why the oft-repeated claim is likely false that most startup go out of business six months after a security breach.
ATM Security Software Found to Have Serious Vulnerability
From DataBreach Today:
ATM Security Software Found to Have Serious Vulnerability
"A security application for ATMs that's designed to thwart "jackpotting" attacks, where cash machines are commanded to surrender their holdings, has been found to have a serious vulnerability.
The software called Checker ATM, developed by the Spanish company GMV, now has a patch. Positive Technologies, a security company, found the vulnerability (CVE-2017-6968), which is a type of memory-related hiccup known as a buffer overflow, in versions 4.x and 5.x."
ATM Security Software Found to Have Serious Vulnerability
"A security application for ATMs that's designed to thwart "jackpotting" attacks, where cash machines are commanded to surrender their holdings, has been found to have a serious vulnerability.
The software called Checker ATM, developed by the Spanish company GMV, now has a patch. Positive Technologies, a security company, found the vulnerability (CVE-2017-6968), which is a type of memory-related hiccup known as a buffer overflow, in versions 4.x and 5.x."
Authorities Take Down Darknet Marketplace
From SecurityWeek:
Authorities Take Down Darknet Marketplace
"Europol announced Thursday that it had assisted the Slovak NAKA crime unit in the arrest of a Slovak national believed to operate a small darknet marketplace dealing in drugs and arms. The individual is in police custody, and several of his premises have been searched.
"In one of the locations searched," says the Europol statement, "Slovak authorities discovered and seized five firearms and approximately 600 rounds of ammunition of different calibres. The investigators also found a sophisticated indoor cannabis plantation, 58 cannabis plants and a Bitcoin wallet containing bitcoins worth EUR 203 000, which is thought to have been obtained from illegal online activities."
Authorities Take Down Darknet Marketplace
"Europol announced Thursday that it had assisted the Slovak NAKA crime unit in the arrest of a Slovak national believed to operate a small darknet marketplace dealing in drugs and arms. The individual is in police custody, and several of his premises have been searched.
"In one of the locations searched," says the Europol statement, "Slovak authorities discovered and seized five firearms and approximately 600 rounds of ammunition of different calibres. The investigators also found a sophisticated indoor cannabis plantation, 58 cannabis plants and a Bitcoin wallet containing bitcoins worth EUR 203 000, which is thought to have been obtained from illegal online activities."
How to Stop a Hacker: Disincentivizing Cybercriminals
From SecurityWeek:
How to Stop a Hacker: Disincentivizing Cybercriminals
"As long as computers have been in existence, there have been people trying to hack them. As technology has evolved and improved, so has the advancements for keeping cyberattacks at bay. But of course, as technology gets smarter, so do the hackers. For years, there has been a ceaseless cycle of organizations finding new ways to secure their data, while hackers continue to find ways to break in and access it.
Cybercriminals, or the “bad” hackers, hack because it’s profitable. A recent report showed that 72 percent of hackers are financially motivated. That means that if the economic incentives were minimized, many may find that it is no longer worthwhile to attempt a cyberattack. Of course, there are many nation state attackers and “hacktivists” who choose to hack for other, non-financial reasons. But for the large majority of cybercriminals attempting to make a buck, it’s important to find ways to deter these criminals from putting forth the effort to attack in the first place."
How to Stop a Hacker: Disincentivizing Cybercriminals
"As long as computers have been in existence, there have been people trying to hack them. As technology has evolved and improved, so has the advancements for keeping cyberattacks at bay. But of course, as technology gets smarter, so do the hackers. For years, there has been a ceaseless cycle of organizations finding new ways to secure their data, while hackers continue to find ways to break in and access it.
Cybercriminals, or the “bad” hackers, hack because it’s profitable. A recent report showed that 72 percent of hackers are financially motivated. That means that if the economic incentives were minimized, many may find that it is no longer worthwhile to attempt a cyberattack. Of course, there are many nation state attackers and “hacktivists” who choose to hack for other, non-financial reasons. But for the large majority of cybercriminals attempting to make a buck, it’s important to find ways to deter these criminals from putting forth the effort to attack in the first place."
Consent Control and eDiscovery: Devils in GDPR Detail
From SecurityWeek:
Consent Control and eDiscovery: Devils in GDPR Detail
"The European General Data Protection Regulation will be in force in just over 12 months: May 25, 2018. This is the date by which all EU nations must have enacted the regulation. Gartner predicts that "by the end of 2018, more than 50 percent of companies affected by the GDPR will not be in full compliance with its requirements."
GDPR will affect all EU-based companies, and all US companies that have any trade with the EU. Despite the threat of hefty non-compliance fines, Gartner is not alone in finding a lack of preparatory urgency among organizations."
Consent Control and eDiscovery: Devils in GDPR Detail
"The European General Data Protection Regulation will be in force in just over 12 months: May 25, 2018. This is the date by which all EU nations must have enacted the regulation. Gartner predicts that "by the end of 2018, more than 50 percent of companies affected by the GDPR will not be in full compliance with its requirements."
GDPR will affect all EU-based companies, and all US companies that have any trade with the EU. Despite the threat of hefty non-compliance fines, Gartner is not alone in finding a lack of preparatory urgency among organizations."
Cisco Patches Critical Flaw in Small Business Router
From SecurityWeek:
Cisco Patches Critical Flaw in Small Business Router
"Cisco has released a firmware update for one of its small business routers to address a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
The vulnerability, discovered by researchers from GeekPwn, a China-based IoT-focused hacking competition, affects CVR100W Wireless-N VPN routers. The company said there was no evidence of malicious exploitation."
Cisco Patches Critical Flaw in Small Business Router
"Cisco has released a firmware update for one of its small business routers to address a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
The vulnerability, discovered by researchers from GeekPwn, a China-based IoT-focused hacking competition, affects CVR100W Wireless-N VPN routers. The company said there was no evidence of malicious exploitation."
Hackers Exploit SS7 Flaws to Loot Bank Accounts
From SecurityWeek:
Hackers Exploit SS7 Flaws to Loot Bank Accounts
"Cybercriminals have exploited vulnerabilities in the SS7 protocol to bypass security mechanisms and steal money from bank accounts. Researchers have warned about the threat for years and these types of attacks have recently become a reality.
SS7, which stands for Signalling System No. 7, is a telephony signaling protocol used by telecommunications providers worldwide. It allows the customers of different networks to communicate with one another and ensures that calls are not interrupted when users are traveling over longer distances."
Hackers Exploit SS7 Flaws to Loot Bank Accounts
"Cybercriminals have exploited vulnerabilities in the SS7 protocol to bypass security mechanisms and steal money from bank accounts. Researchers have warned about the threat for years and these types of attacks have recently become a reality.
SS7, which stands for Signalling System No. 7, is a telephony signaling protocol used by telecommunications providers worldwide. It allows the customers of different networks to communicate with one another and ensures that calls are not interrupted when users are traveling over longer distances."
FBI: Business- and Email Account Compromise Attack Losses Hit $5 Billion
From Dark Reading:
FBI: Business- and Email Account Compromise Attack Losses Hit $5 Billion
"The FBI's IC3 division reports a 2,370% spike in exposed losses resulting from BEC and EAC between January 2015 and December 2016.
The FBI's Internet Crime Complaint Center (IC3) reports business email compromise (BEC) and email account compromise (EAC) attacks caused $5.3 billion in exposed loss for global and domestic companies between October 2013 and December 2016. Victims, which come from 50 states and 131 countries, reported a total of 40,203 incidents in the same time period."
FBI: Business- and Email Account Compromise Attack Losses Hit $5 Billion
"The FBI's IC3 division reports a 2,370% spike in exposed losses resulting from BEC and EAC between January 2015 and December 2016.
The FBI's Internet Crime Complaint Center (IC3) reports business email compromise (BEC) and email account compromise (EAC) attacks caused $5.3 billion in exposed loss for global and domestic companies between October 2013 and December 2016. Victims, which come from 50 states and 131 countries, reported a total of 40,203 incidents in the same time period."
Attackers Unleash OAuth Worm via 'Google Docs' App
From DataBreach Today:
Attackers Unleash OAuth Worm via 'Google Docs' App
"A malicious app named "Google Docs" by attackers has been making the rounds, attempting to trick Google users into logging in and giving the app access permissions to their account.
The phishing campaign began with an email to victims from an address they likely would have recognized, according to multiple analyses of the attack that have now been posted online by security researchers. But the campaign quickly turned into a worm, as users authorized the bogus app in droves, allowing it to spread to their own contacts."
Attackers Unleash OAuth Worm via 'Google Docs' App
"A malicious app named "Google Docs" by attackers has been making the rounds, attempting to trick Google users into logging in and giving the app access permissions to their account.
The phishing campaign began with an email to victims from an address they likely would have recognized, according to multiple analyses of the attack that have now been posted online by security researchers. But the campaign quickly turned into a worm, as users authorized the bogus app in droves, allowing it to spread to their own contacts."
HTTP Headers... the Achilles' heel of many applications
From SANS ISC:
HTTP Headers... the Achilles' heel of many applications
"When browsing a target web application, a pentester is looking for all “entry” or “injection” points present in the pages. Everybody knows that a static website with pure HTML code is less juicy compared to a website with many forms and gadgets where visitors may interact with it. Classic vulnerabilities (XSS, SQLi) are based on the user input that is abused to send unexpected data to the server. Here is a very simple GET example:"
HTTP Headers... the Achilles' heel of many applications
"When browsing a target web application, a pentester is looking for all “entry” or “injection” points present in the pages. Everybody knows that a static website with pure HTML code is less juicy compared to a website with many forms and gadgets where visitors may interact with it. Classic vulnerabilities (XSS, SQLi) are based on the user input that is abused to send unexpected data to the server. Here is a very simple GET example:"
US-CERT Alert: IC3 Warns of Increase in BEC/EAC Schemes
From US-CERT:
IC3 Warns of Increase in BEC/EAC Schemes
"The Internet Crime Complaint Center (IC3) has issued an alert describing a growing number of scams targeting businesses working with foreign suppliers or businesses that regularly perform wire transfer payments. These sophisticated scams are classified as business email compromise (BEC) or email account compromise (EAC) and use social engineering techniques to defraud businesses."
IC3 Warns of Increase in BEC/EAC Schemes
"The Internet Crime Complaint Center (IC3) has issued an alert describing a growing number of scams targeting businesses working with foreign suppliers or businesses that regularly perform wire transfer payments. These sophisticated scams are classified as business email compromise (BEC) or email account compromise (EAC) and use social engineering techniques to defraud businesses."
Unpatched WordPress Password Reset Vulnerability Lingers
From ThreatPost:
Unpatched WordPress Password Reset Vulnerability Lingers
"A zero-day vulnerability exists in WordPress Core that in some instances could allow an attacker to reset a user’s password and gain access to their account.
Researcher Dawid Golunski of Legal Hackers disclosed the vulnerability on Wednesday via his new ExploitBox service. All versions of WordPress, including the latest, 4.7.4, are vulnerable, the researcher said."
Unpatched WordPress Password Reset Vulnerability Lingers
"A zero-day vulnerability exists in WordPress Core that in some instances could allow an attacker to reset a user’s password and gain access to their account.
Researcher Dawid Golunski of Legal Hackers disclosed the vulnerability on Wednesday via his new ExploitBox service. All versions of WordPress, including the latest, 4.7.4, are vulnerable, the researcher said."
OSX.Bella: Mac Malware Strikes Again
From Dark Reading:
OSX.Bella: Mac Malware Strikes Again
"This variant of the OSX.Dok dropper behaves altogether differently, and installs a completely different payload.
On Friday, a sophisticated Mac Trojan was discovered called OSX.Dok, which installs malware designed to intercept all HTTP and HTTPS traffic. This morning, Adam Thomas, a Malwarebytes researcher, found a variant of the OSX.Dok dropper that behaves altogether differently and installs a completely different payload."
OSX.Bella: Mac Malware Strikes Again
"This variant of the OSX.Dok dropper behaves altogether differently, and installs a completely different payload.
On Friday, a sophisticated Mac Trojan was discovered called OSX.Dok, which installs malware designed to intercept all HTTP and HTTPS traffic. This morning, Adam Thomas, a Malwarebytes researcher, found a variant of the OSX.Dok dropper that behaves altogether differently and installs a completely different payload."
Europe Pumps Out 50% More Cybercrime Attacks Than US
From Dark Reading:
Europe Pumps Out 50% More Cybercrime Attacks Than US
"Cyberattacks originating from Europe were substantially higher than nefarious activity launched from the US during the first quarter.
Cybercrime attacks launched from Europe reached more than 50 million in the first quarter, double the volume coming out of the US, according to the ThreatMetrix Q1 Cybercrime Report released today."
Europe Pumps Out 50% More Cybercrime Attacks Than US
"Cyberattacks originating from Europe were substantially higher than nefarious activity launched from the US during the first quarter.
Cybercrime attacks launched from Europe reached more than 50 million in the first quarter, double the volume coming out of the US, according to the ThreatMetrix Q1 Cybercrime Report released today."
Google Docs Phishing Scam a Game Changer
From Dark Reading:
Google Docs Phishing Scam a Game Changer
"Experts expect copycats that take advantage of passive authentication from third-party applications using standards such as OAuth.
The Google Doc phishing scam that conned over a million users this week illustrates how attackers cleverly respond to wider spread end-user awareness about how phishing attacks work."
Google Docs Phishing Scam a Game Changer
"Experts expect copycats that take advantage of passive authentication from third-party applications using standards such as OAuth.
The Google Doc phishing scam that conned over a million users this week illustrates how attackers cleverly respond to wider spread end-user awareness about how phishing attacks work."
Going travelling? Don’t drop your guard when you’re on the road
From Sophos Naked Security:
Going travelling? Don’t drop your guard when you’re on the road
"As the hotel industry has been discovering to its cost, cybercriminals are a part of the population that doesn’t seem to take holidays.
Recent days have seen an unspecified possible breach in the reservation payment systems run by US company Sabre for 32,000 hotels and lodges, which prompted it to call forensics Ghostbusters Mandiant to work out what’s been haunting its network."
Going travelling? Don’t drop your guard when you’re on the road
"As the hotel industry has been discovering to its cost, cybercriminals are a part of the population that doesn’t seem to take holidays.
Recent days have seen an unspecified possible breach in the reservation payment systems run by US company Sabre for 32,000 hotels and lodges, which prompted it to call forensics Ghostbusters Mandiant to work out what’s been haunting its network."
Celebrity ‘extortion’: judge orders reality star to unlock her iPhone
From Sophos Naked Security:
Celebrity ‘extortion’: judge orders reality star to unlock her iPhone
"A Miami judge on Wednesday ordered a reality TV star to unlock her iPhone in a case that’s yet again firing up the legal debate around when we can be compelled to give up our passcodes.
The star, Hencha Voigt, has been charged with conspiracy to extort a social-media celebrity known as the “Queen of Snapchat”. The target of the alleged extortion was South Beach socialite YesJulz (pictured), whose real name is Julieanne Goddard. She’s a party promoter and online marketer who hangs with rappers and athletes and boasts hundreds of thousands of followers, according to her publicist."
Celebrity ‘extortion’: judge orders reality star to unlock her iPhone
"A Miami judge on Wednesday ordered a reality TV star to unlock her iPhone in a case that’s yet again firing up the legal debate around when we can be compelled to give up our passcodes.
The star, Hencha Voigt, has been charged with conspiracy to extort a social-media celebrity known as the “Queen of Snapchat”. The target of the alleged extortion was South Beach socialite YesJulz (pictured), whose real name is Julieanne Goddard. She’s a party promoter and online marketer who hangs with rappers and athletes and boasts hundreds of thousands of followers, according to her publicist."
The Bondnet Army
A technical overview of the Bondnet Army botnet from GuardiCore:
The Bondnet Army
"GuardiCore Labs has recently picked up Bondnet, a botnet of thousands of compromised servers of varying power. Managed and controlled remotely, the Bondnet is currently used to mine different cryptocurrencies and is ready to be weaponized immediately for other purposes such as mounting DDoS attacks as shown by the Mirai Botnet. Among the botnet’s victims are high profile global companies, universities, city councils and other public institutions."

The Bondnet Army
"GuardiCore Labs has recently picked up Bondnet, a botnet of thousands of compromised servers of varying power. Managed and controlled remotely, the Bondnet is currently used to mine different cryptocurrencies and is ready to be weaponized immediately for other purposes such as mounting DDoS attacks as shown by the Mirai Botnet. Among the botnet’s victims are high profile global companies, universities, city councils and other public institutions."

Thursday, May 4, 2017
FTC Alert: Who's really calling?
From the Federal Trade Commission:
Who's really calling?
"The millions of people who reported scams last year told us that imposters were the top fraud of the year. Imposters have called many of us – maybe even most of us, pretending to be anyone from the IRS to a family member in trouble, from fake tech “help” for your computer to a business selling things that turned out to be bogus. Their goal? To get your money as quickly as possible."
Who's really calling?
"The millions of people who reported scams last year told us that imposters were the top fraud of the year. Imposters have called many of us – maybe even most of us, pretending to be anyone from the IRS to a family member in trouble, from fake tech “help” for your computer to a business selling things that turned out to be bogus. Their goal? To get your money as quickly as possible."
How does the boot mode vulnerability in Android work?
From SearchSecurity:
How does the boot mode vulnerability in Android work?
"Google recently shut down the boot mode vulnerability in Android that allowed hackers to eavesdrop on calls. Can you explain how this exploit works?
It takes a few steps for the boot mode vulnerability exploit to work. First, the attacker infects a PC with malware through the internet. Then, the attacker waits for the victim to enable Android Debug Bridge (ADB) after manually connecting his Nexus 6 or 6P phone to the infected PC."
How does the boot mode vulnerability in Android work?
"Google recently shut down the boot mode vulnerability in Android that allowed hackers to eavesdrop on calls. Can you explain how this exploit works?
It takes a few steps for the boot mode vulnerability exploit to work. First, the attacker infects a PC with malware through the internet. Then, the attacker waits for the victim to enable Android Debug Bridge (ADB) after manually connecting his Nexus 6 or 6P phone to the infected PC."
Macon teen’s Facebook Live suicide attempt is stopped by deputies
From The (Macon) Telegraph:
Macon teen’s Facebook Live suicide attempt is stopped by deputies
The haunting scene unfolded on digital screens about 7:30 p.m., prompting several to call 911."
Read more here: http://www.macon.com/news/local/article148495809.html#storylink=cpy
Macon teen’s Facebook Live suicide attempt is stopped by deputies
The haunting scene unfolded on digital screens about 7:30 p.m., prompting several to call 911."
Read more here: http://www.macon.com/news/local/article148495809.html#storylink=cpy
7 Steps to Fight Ransomware
From Dark Reading:
7 Steps to Fight Ransomware
"Perpetrators are shifting to more specific targets. This means companies must strengthen their defenses, and these strategies can help.
Ransomware can be a highly lucrative system for extracting money from a customer. Victims are faced with an unpleasant choice: either pay the ransom or lose access to the encrypted files forever. Until now, ransomware has appeared to be opportunistic and driven through random phishing campaigns. These campaigns often, but not always, rely on large numbers of emails that are harvested without a singular focus on a company or individual."
7 Steps to Fight Ransomware
"Perpetrators are shifting to more specific targets. This means companies must strengthen their defenses, and these strategies can help.
Ransomware can be a highly lucrative system for extracting money from a customer. Victims are faced with an unpleasant choice: either pay the ransom or lose access to the encrypted files forever. Until now, ransomware has appeared to be opportunistic and driven through random phishing campaigns. These campaigns often, but not always, rely on large numbers of emails that are harvested without a singular focus on a company or individual."
Small Budgets Cripple Cybersecurity Efforts of Local Governments
From Dark Reading:
Small Budgets Cripple Cybersecurity Efforts of Local Governments
"A survey of local government chief information officers finds that insufficient funding for cybersecurity is the biggest obstacle in achieving high levels of cyber safety.
Inadequate budgets are the largest obstacle for local government chief information officers in obtaining the highest level of cybersecurity for their organization, according to a survey released today by the International City/County Management Association."
Small Budgets Cripple Cybersecurity Efforts of Local Governments
"A survey of local government chief information officers finds that insufficient funding for cybersecurity is the biggest obstacle in achieving high levels of cyber safety.
Inadequate budgets are the largest obstacle for local government chief information officers in obtaining the highest level of cybersecurity for their organization, according to a survey released today by the International City/County Management Association."
Google Docs Phishing Attack Abuses Legitimate Third-Party Sharing
From Dark Reading:
Google Docs Phishing Attack Abuses Legitimate Third-Party Sharing
"Phishing messages appear nearly identical to legitimate requests to share Google documents, because in many ways, they are.
Google users today were hit with an extremely convincing phishing spree launched by attackers who manipulated Google Docs' legitimate third-party sharing mechanism."
Google Docs Phishing Attack Abuses Legitimate Third-Party Sharing
"Phishing messages appear nearly identical to legitimate requests to share Google documents, because in many ways, they are.
Google users today were hit with an extremely convincing phishing spree launched by attackers who manipulated Google Docs' legitimate third-party sharing mechanism."
Tinder orders researcher to remove dataset of 40,000 profile pictures
From Sophos Naked Security:
Tinder orders researcher to remove dataset of 40,000 profile pictures
"Following a privacy kerfluffle, Tinder told a developer to remove a dataset of 40,000 of its users’ images that he had published in six downloadable zip files and released under a CC0: Public Domain License.
The dataset was called People of Tinder.
The developer, Stuart Colianni, who not-so-charmingly referred to the Tinder users as “hoes” in his source code, was using the images to train artificial intelligence."
Tinder orders researcher to remove dataset of 40,000 profile pictures
"Following a privacy kerfluffle, Tinder told a developer to remove a dataset of 40,000 of its users’ images that he had published in six downloadable zip files and released under a CC0: Public Domain License.
The dataset was called People of Tinder.
The developer, Stuart Colianni, who not-so-charmingly referred to the Tinder users as “hoes” in his source code, was using the images to train artificial intelligence."
Concern mounts at Indian ID scheme as portals ‘leak’ 100m people’s details
From Sophos Naked Security:
Concern mounts at Indian ID scheme as portals ‘leak’ 100m people’s details
"The details of more than 100m Indians’ Aadhaar ID cards have leaked from four government portals, according to a report from the Centre for Internet and Society (CIS).
Concern mounts at Indian ID scheme as portals ‘leak’ 100m people’s details
"The details of more than 100m Indians’ Aadhaar ID cards have leaked from four government portals, according to a report from the Centre for Internet and Society (CIS).
Based on the numbers available on the websites looked at, [the] estimated number of Aadhaar numbers leaked through these four portals could be around 130-135 million"
NSA collected records of 151m Americans – but wait, didn’t bulk collection stop three years ago?
From Sophos Naked Security:
NSA collected records of 151m Americans – but wait, didn’t bulk collection stop three years ago?
"You remember the NSA’s bulk phone data collection program, right?
As in, the one that Congress cut the funding for in 2014? The one that wasn’t authorized by Section 215 of the Patriot Act after all, as a court unanimously ruled in 2015? … but which got extended anyway?
Boy, did it get extended, and how. It’s still chugging along just fine."
NSA collected records of 151m Americans – but wait, didn’t bulk collection stop three years ago?
"You remember the NSA’s bulk phone data collection program, right?
As in, the one that Congress cut the funding for in 2014? The one that wasn’t authorized by Section 215 of the Patriot Act after all, as a court unanimously ruled in 2015? … but which got extended anyway?
Boy, did it get extended, and how. It’s still chugging along just fine."
Update: Google Doc phishing story takes some bizarre turns
From Sophos Naked Security:
Update: Google Doc phishing story takes some bizarre turns
"Since news began circulating last night of a phishing campaign parading around as Google Doc access links, the tale has taken strange twists and turns.
A self-described graduate student claims he was behind the blast of emails, and that they were part of a test for a school project, not a phishing attack. But according to the university he claims to be enrolled at, he’s not a student there."
Update: Google Doc phishing story takes some bizarre turns
"Since news began circulating last night of a phishing campaign parading around as Google Doc access links, the tale has taken strange twists and turns.
A self-described graduate student claims he was behind the blast of emails, and that they were part of a test for a school project, not a phishing attack. But according to the university he claims to be enrolled at, he’s not a student there."
FYI - to help reduce the attack surface block:
hhhhhhhhhhhhhhhh @ mailinator . com
on your email system(s).
US-CERT Alert: Microsoft Ending Security Updates for Windows 10 version 1507
From US-CERT:
Microsoft Ending Security Updates for Windows 10 version 1507
"After May 9, 2017, devices running Windows 10 version 1507 will no longer receive security updates."
Microsoft Ending Security Updates for Windows 10 version 1507
"After May 9, 2017, devices running Windows 10 version 1507 will no longer receive security updates."
US-CERT Alert: Cisco Releases Security Updates
From US-CERT:
Cisco Releases Security Updates
"Cisco has released updates to address vulnerabilities affecting multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system."
Cisco Releases Security Updates
"Cisco has released updates to address vulnerabilities affecting multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system."
Wednesday, May 3, 2017
OAUTH phishing against Google Docs ? beware!
From SANS ISC:
OAUTH phishing against Google Docs ? beware!
We got several reports (thanks to Seren Thompson, Tahir Khan and Harry Vann) about OAUTH phishing attacks against Google users. The phishing attack arrives, of course, as an e-mail where it appears that a user (potentially even one on your contact list, so it looks very legitimate) has shared a document.
An image of such an e-mail is shown below:
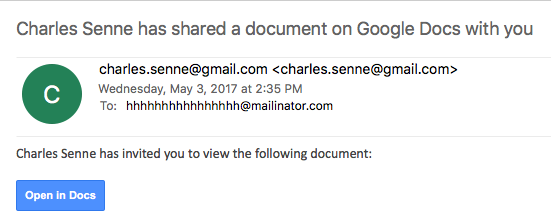
OAUTH phishing against Google Docs ? beware!
We got several reports (thanks to Seren Thompson, Tahir Khan and Harry Vann) about OAUTH phishing attacks against Google users. The phishing attack arrives, of course, as an e-mail where it appears that a user (potentially even one on your contact list, so it looks very legitimate) has shared a document.
An image of such an e-mail is shown below:

Subscribe to:
Comments (Atom)